LinkedIn app under scrutiny for transferring iOS calendar entries
Skycure's Yair Amit and Adi Sharabani revealed their discovery ahead of a presentation at Tel Aviv University on Wednesday, The New York Times' Bits blog reports. Though the app's syncing feature does require a user's approval, the researchers criticized it for unnecessarily transmitting calendar entries and doing so in an unsecure manner.
“In some cases, grabbing users’ sensitive data might be O.K. It is never right to do so without a clear indication. It is far worse when the sensitive information is not really needed in the first place. This is what we found in LinkedIn,†said Sharabani.
A spokeswoman from LinkedIn acknowledged the feature as a "clear 'opt-in' experience" and noted that it syncs to the company's servers only when the app is open.
“We use information from the meeting data to match LinkedIn profile information about who you’re meeting with so you have more information about that person,†said spokeswoman Julie Inouye.
The company also responding with a blog post explaining the feature. The post clarified that the data is being sent over a secure SSL connection and is not stored on LinkedIn's servers. Author Joff Redfern, the company's mobile product head, pledged to stop sending meeting notes and to provide a link to more information about how the data is being used.
However, Amit and Sharabani maintained that LinkedIn would only need "unique identifiers" for users and not all of the calendar information. To prove their point, they demonstrated how the password for a confidential financial conference call was being transmitted to the company's servers.
Source: The New York Times
LinkedIn was among a number of companies contacted by U.S. congressmen in March to address concerns over information collection and privacy.
The rise of the so-called "app economy" has made the issue of mobile application privacy a hot topic among researchers, legislators and privacy advocates. Earlier this year, the Path app was discovered to be uploading users' address books to servers. Path CEO Dave Morin quickly apologized and promised to delete the information. Apple CEO Tim Cook reportedly was upset by the revelation and "grilled" Morin over the issue at Apple's headquarters in Cupertino, Calif.
Apple has made its own changes in iOS to protect user privacy. Starting with iOS 5, Apple began deprecating developer access to unique device identifiers. Developers reported in March that Apple was rejecting apps that accessed UDIDs. Apple recently published a detailed guide geared toward enterprise customers that outlined the security features in iOS.
However, advertising companies have found workarounds to compensate for the loss of UDID tracking. One recent report suggested that ad networks are now using Open Device Identification Network and OpenUDID standards as substitutes.
 Josh Ong
Josh Ong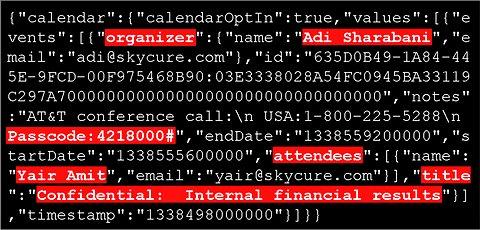










 Mike Wuerthele
Mike Wuerthele

 Malcolm Owen
Malcolm Owen
 Chip Loder
Chip Loder

 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Michael Stroup
Michael Stroup