iOS Location authorization loophole gives apps access to iDevice photos
In a report on Tuesday, The New York Times outlined the issue that allows an app to upload geo-tagged photos from an iPhone, iPad or iPod touch in an unseen background task after said app has received permission from the user to enable location services.
Developers have been aware that the so-called "loophole" has existed for some time now, though until now there has been no proof-of-concept showing the functionality's scope. To that end, The Times asked a developer, who requested not to be named due to his association with a major app company, to write a test program that exploited the purported security weakness.
The code writer created "PhotoSpy" which, once installed and launched on an iPhone testbed, first asks for access to a user's location data. Once granted, the app begins the process of uploading photos and their corresponding location data to a remote server.
“Conceivably, an app with access to location data could put together a history of where the user has been based on photo location,†said app maker Curio's co-founder David E. Chen. “The location history, as well as your photos and videos, could be uploaded to a server. Once the data is off of the iOS device, Apple has virtually no ability to monitor or limit its use.â€
Test app PhotoSpy's location authorization pop-up. Source| The New York Times
Typical Apple safeguards have been to sandbox apps, or limit their access to data and certain system-level iOS functions. When the company's mobile platform changed from "iPhone OS" to "iOS" in 2010, the sandbox grew to include the photo library among other system services.
Apple still has theoretical control over possibly malicious apps as software that reaches the App Store must first pass through the company's vetting process. However, the company has shown some missteps recently as the number of apps being submitted to the store is swelling.
An example would be the fake "Pokemon" app that made it into the App Store and reached top-five most-downloaded status before being pulled.
In attempts to streamline user experience and make a more cohesive product, developers have been looking for ways to consolidate data behind the scenes though some of their efforts border on invasion of privacy.
Earlier in February, the social networking app "Path" came under fire for uploading users' addresses in a background task in a reported attempt to make connecting with other friends using the program a seamless process. Customer backlash prompted the developer of the program to institute an opt-in requirement and issue an apology.
“Apple has a tremendous responsibility as the gatekeeper to the App Store and the apps people put on their phone to police the apps,†said David Jacobs, a fellow with the Electronic Privacy Information Center. “Apple and app makers should be making sure people understand what they are consenting to. It is pretty obvious that they aren’t doing a good enough job of that.â€
 Mikey Campbell
Mikey Campbell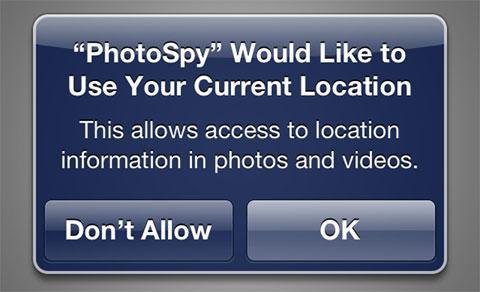











 Wesley Hilliard
Wesley Hilliard
 Amber Neely
Amber Neely

 William Gallagher
William Gallagher

 Malcolm Owen
Malcolm Owen