New Mac OS X Trojan disguises itself as Adobe Flash installer
The Trojan Horse, discovered by security firm Intego, has been found on malicious web sites that invite users to install the phony Flash Player, telling them it is required to access certain content. Since Mac OS X Lion doesn’t come with Flash preinstalled, users must manually install it. Intego categorized the threat from Flashback as "low."
The new malware is said to specifically target Lion, and replicates the look and feel of the real Flash installer. It includes design elements and logos that could convince some users it is the actual official software from Adobe.
Once the Trojan is installed on the system, it will delete the installer package and deactivate some network security software. The code used by Flashback can be injected in certain applications run on the computer and the Trojan can connect to remote servers in order to send specific information about the infected computer — including its MAC address, which is a unique identifier for every machine.
Lion users can protect themselves by downloading the official Flash Player installation player from Adobe. Users should also check the origin of any file claiming to be a Flash Player installer.
Users should also uncheck the "Open 'safe' files after downloading" option in Apple's Safari browser under General Preferences. This will help ensure that the Flashback installer is not automatically run if downloaded.
Users can also manually check to see whether they were infected by looking for the file "~/Library/Preferences/Preferences.dylib" on their Mac.
Apple has already distributed a malware definition update to block another Trojan horse, “Trojan-Dropper:OSX/Revir.A,†described late last week as a malicious program posing as a PDF download.
 Chris Smith
Chris Smith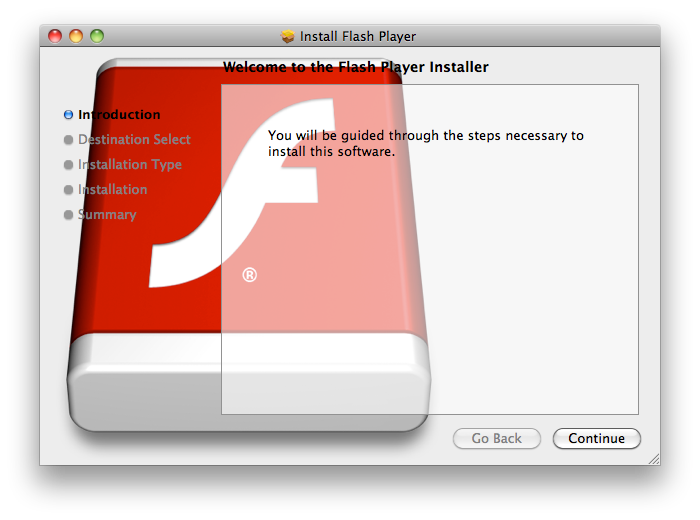











 Mike Wuerthele
Mike Wuerthele
 Malcolm Owen
Malcolm Owen
 Chip Loder
Chip Loder

 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Michael Stroup
Michael Stroup
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele







