Researchers discover PDF malware that targets Apple's Mac OS X
The trojan, identified as Trojan-Dropper:OSX/Revir.A, opens a botnet backdoor by tricking the user into downloading and opening a Chinese language PDF file while it installs itself in the background, according to security researchers at F-Secure.
The command-and-control center of the trojan is currently a bare Apache installation that has been sitting dormant at its domain since May and is not yet capable of communicating with any backdoors. This has led researchers to believe that they have found a malware in the making.
Trojans typically mask themselves as a PDF and infect systems while the user is busy opening the file. But researchers believe that this particular sample may be stealthier than usual malware.
The new trojan differs from most Windows PDF malware in that it arrived to researchers without the usual "pdf.exe" extension or icon. Researchers note that because extension and icon data are stored and displayed differently on Macs, this sample could be more difficult to detect than Windows counterparts, as it can adopt any extension desired.
The technique of using a PDF file as a ruse for the propagation of malware has been a mainly Windows problem in the past, remaining a minimal threat to Mac users.
It is unclear how this malware is spreading, but researchers believe that the most likely mode of circulation is via e-mail attachment. The researchers suggested the author of the trojan could simply be "testing the water" to see if their creation is identified by various antivirus applications.
 Mikey Campbell
Mikey Campbell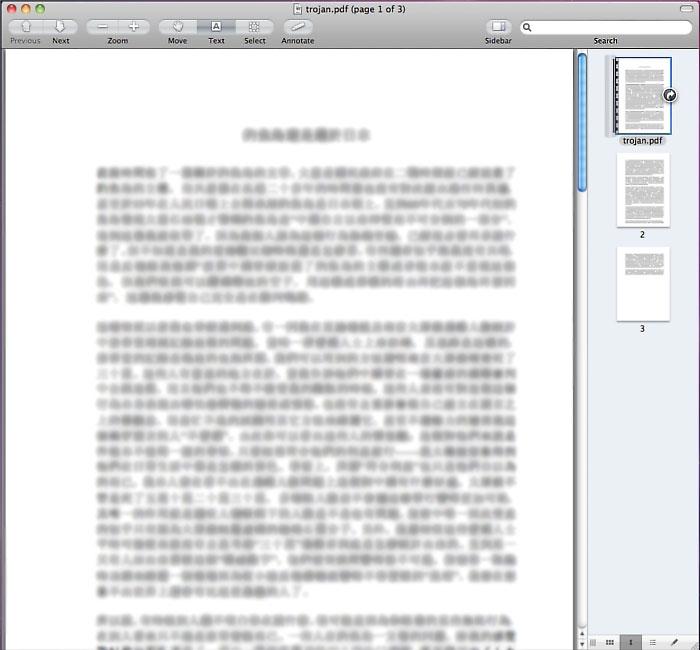










 Mike Wuerthele
Mike Wuerthele

 Malcolm Owen
Malcolm Owen
 Chip Loder
Chip Loder

 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Michael Stroup
Michael Stroup







