Latest 'MAC Defender' malware attacks Mac OS X without password
The discovery was announced on Wednesday by security firm Intego. Unlike previous versions of the software, which required users to enter an administrator password to install the fake antivirus, the latest variant uses a different install method.
"The first part is a downloader, a tool that, after installation, downloads a payload from a web server," the security firm said. "As with the Mac Defender malware variants, this installation package, called avSetup.pkg, is downloaded automatically when a user visits a specially crafted web site."
No administrator's password is required to install the application, and if users have Safari's "Open 'safe' files after downloading option checked, the package will open Apple's Mac OS X installer, and users will see a standard installation screen. However, at this point users must still agree to install the "MAC Defender" malware.
The second part of the malware is a new version called "MacGuard." The avRunner application automatically downloads "MacGuard," which, like its predecessor, aims to trick users into providing credit card numbers in exchange for supposedly ridding a users' systems of "infected" files.
This week, Apple posted instructions on its website explaining how to remove the "MAC Defender" malware. The company also revealed it will release an update to its Mac OS X operating system that will automatically find and remove the malware.
Some reports have suggested that the "MAC Defender" malware has spread quickly, with one anonymous AppleCare representative claiming that the "overwhelming majority" of recent calls to Apple were related to the malware. The software was first discovered early this month, also by Intego.
While the original variant was categorized as a "low" threat because it requires users to type in an administrator password, the latest version is considered more dangerous, and was ranked with a "medium" risk.
The malware has spread through search engines like Google via a method known as "SEO poisoning." Using this technique, phony sites are designed to game search engine algorithms and show up when users search for certain topics.
 Slash Lane
Slash Lane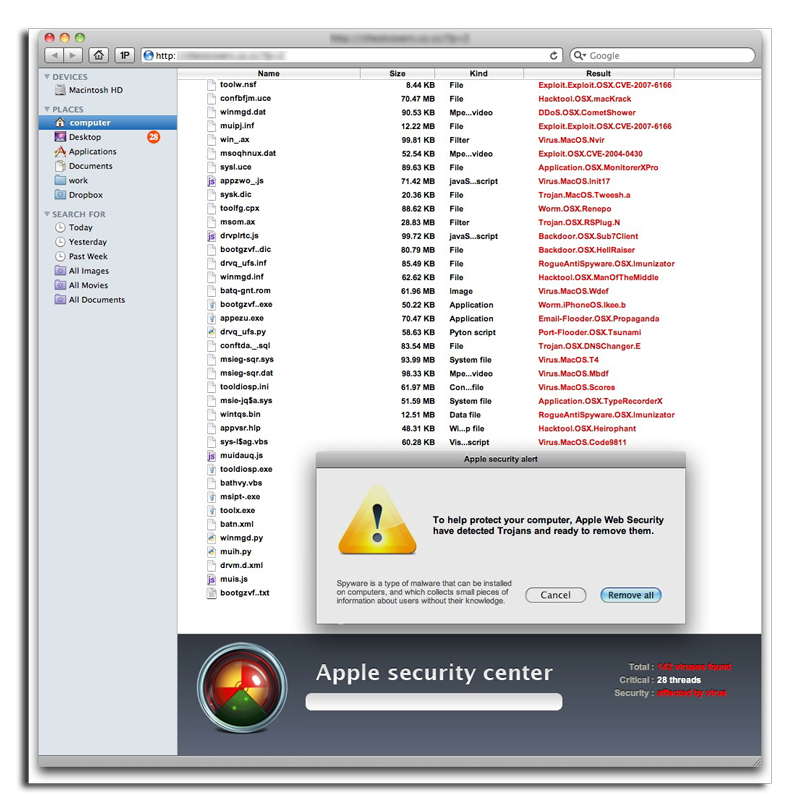











 Marko Zivkovic
Marko Zivkovic
 David Schloss
David Schloss

 Malcolm Owen
Malcolm Owen

 William Gallagher
William Gallagher
 Mike Wuerthele
Mike Wuerthele
 Christine McKee
Christine McKee







